Schemes-Draft
Passwords are a major problem to manage. Ideally, every password you use should be unique to the given service. This tends to be impractical when you have a lot of systems you connect to. It is easy to use the same passwords in multiple places, but this will lead to compromised access in multiple places.
Keep in mind that the password you use is stored someplace on every service you use it on. Frequently these places will store them insecurely. They may store the password in plain text, or using a weak password hash. Even a strong password hash can be broken using a brute force attack. This means its only a matter of time before your password will be exposed.
WARNING: Do not use any of the passwords given as examples here or anywhere else. Any publicly disclosed password will eventually find its way into a password dictionary for use in a brute force attack. The same happens with compromised password files even if not publicly available, you can bet a compromised password file will be brute force attacked and all passwords discovered will be added to a hackers password dictionary.
Ideal Password
Passwords should contain a mix of upper and lower case letters, numbers, and symbols. They should be at least 8 characters long and should look like random noise. k*2C54!qj43 is a good password, but is really hard to remember. The idea is to get something that looks like that, but is easy for you to remember.
Password Categories
One way to help reduce the risk of a compromised password is to set security categories for your passwords. This way you can reuse passwords or password variants with lower risks as a consequence of a compromise. Password schemes used should be completely different between categories to reduce the chance of a compromise in one category effecting other categories.
For example, your bank accounts should have a high security level. Ideally it should be a unique password for each account, but maybe instead you use a password variant system that makes it easy to remember all the passwords in this category. Your social media accounts you might consider to be medium risk so you use a different set of passwords then you use for your banking information. This means a compromise in a social media account wont lead to a compromise to your banking information.
Password Variants
One scheme commonly employed is to use a common root for your passwords, but with a part that varies for each password in the set. For example, you could use 'password' as your root, and add a date to it like this: password2020, password1970, password1990, etc. These are all terrible passwords, but give you the idea.
It'd be better to use something less obvious in your password variants. For instance, you could use a substitution scheme for the part of the password that changes. For example, for your bank accounts you might use the first and last digit of your bank account number, but mix in something else with it like some letters representing the colour of their logo. So, say you have a bank that uses Green in its logo and your first digit of your account is 1 and the last is 8, you could use password1gn8, or password8g1n, etc.
This is better, and harder for a cracker to guess what the varying part represents, but easy for you to remember. A second bank using orange in its logo could look like this: password7o8r. The use of password, or any dictionary word for that matter isn't good though. It'd be better to also obscure that part, but not in a way that is obvious. So pa$$w0rd, may look more secure, but it isn't. $ is commonly used to replace s and 0 is commonly used to replace o. A brute force attack can easily incorporate such variants into their attach.
A better idea would be to generate your fixed portion of the password using a different substitution method. A phrase of 'my secrete password' could be used to generate something like mySTpw as your fixed portion of your varying password scheme. And you might want to add a symbol between the fixed and varying parts of the password so you end up with something like this: mySTpw&1gn8. That looks much more like random gibberish, while still being easy to remember.
Password Substitution Schemes
As mentioned in the above examples, you can generate a password from something using simple substitution schemes. This can be as simple as using letters from a word, replacing a word with a symbol, or inserting numbers or symbols into a word. So a passphrase of 'my secrete password' could be 'mySTpw' like above, or maybe my&pw', or 'm!s^p'.
A common substitution scheme is to use the names of your pets or children in a password. This is generally a bad idea because its personal information about you that someone can find out. So instead of using the name, use a common substitution for that name in your pass phrase. So if you have a cat named 'Fluffy', and a son named 'Tommy' you could replace that with cF and sT, or c& and *T, or whatever makes sense to you. Then a passphrase of 'My cat plays fetch' could be turned into something like 'mYc&plays>'. 'My son plays fetch with fluffy' could become 'M*Tplays>cF'.
Both of these are good, but neither have numbers in them. So you could maybe add them to the substitutions for the names. Say your cat was born in 2018, so cF18 could represent your cat in a password. and your son Tommy might be your second son so 2*T. Making the passphrase above 'M2*Tplays>cF18'. The whole word plays is a dictionary word, so not recommended on its own, but mixed with the rest, that is actually a very good password. But you could shorten it by replacing it, or just remove it. 'M2*T>cF18'. That is plenty strong enough on its own, and easy to remember; Fluffy and Tommy are playing.
2*T and cF18 can be used in multiple passwords exactly as they are. They're easy to remember and have significant meaning to you that isn't obvious to others. As such, they make good building blocks for any passphrase.
Shocking Nonsense
One of the best password schemes I ever heard of (I wish I know where from so I could give proper credit), is known as Shocking Nonsense. The basic concept is to come up with a passphrase that you yourself find shocking. This has two benefits. First we tend to remember things we find shocking. Second, we tend not to want to share it with others so you wont be giving it out to anyone. ;)
It's best if the phrase is something you find shocking and is generally against your own personality. So, if you never swear, put some swear words in it. Use inappropriate or violent imagery in it. Make it personal about yourself or someone you know that you yourself are offended by. It should be something you personally find horrifying that you could have thought up. Even better if you would be mortified to share it publicly. You'll find you never forget it, and you never share it! :)
So, obviously we need to keep this document mostly clean, so we'll work with the passphrase 'Feed exploding puppies to troubled children'. You can replace feed with F; exploding could be !; puppies could be the substitution you use for a your own pet like cF18 from above; troubled could be TR; and children could be kids. So you end up with F!cF18TRkids. That a pretty good password, and you're likely not going to forget the passphrase for a long time. :)
Wikipedia Facts and Figures
A password scheme I came up with involves using wikipedia to generate passwords. The basic idea is to search something on wikipedia or other data source that contains a lot of facts and figures; ideally a page with a chart. Since things on wikipedia tend to change over time, you'll want to save or print the page or chart. This can be done using a chart from a published book also.
The idea is to take a chart of data and use it to generate your passwords. That chart can then be placed someplace in plan site, but on its own it isn't obvious its the key to your passwords. Take for instance this page from wikipedia. It contains this chart:
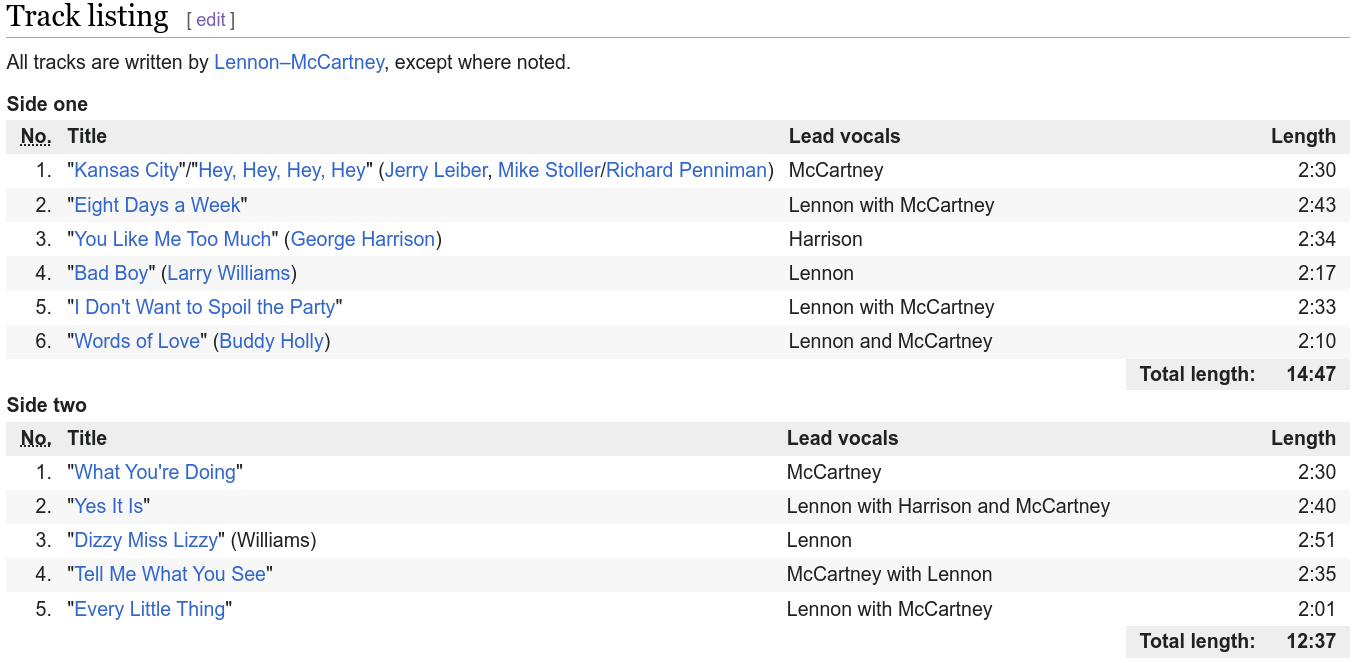
Using this chart, we could make a password from the song "Words of Love". The basic facts from the chart are that it is song #6 from side 1 of the album (1#6). It's play time is 2:10, was written by Buddy Holly, and sung by John Lennon and Paul McCartney. So, to make it simple, we'll convert the names to initials BH, JL, PM. We'll do the same for the song title, but make it all lower case (wol). 2:10 is easy to remember so we'll use that. Put it all together you get something like this: wolBH1#6JLPM2:10. That's a really good password! Perhaps a little too long, so just change what you include in your password. You could make a bunch of passwords from that one line on the chart. If you ever forget, you just have to look at the chart and remember the scheme you used. You could pin it to the wall or include it on a pmwiki page like this in plain site. Nobody would have a clue except you.
